Understanding Multisig: A Key to Enhanced Crypto Security
In the world of cryptocurrency, security is paramount. With the increasing value of digital assets, protecting them from unauthorized access is a top priority. One of the most effective security measures in the crypto world is the use of multisig, or multi-signature, wallets. But what exactly is multisig, and how does it work? Let’s break it down in simple terms.
What is Multisig?
In essence, a multisig wallet is like a digital safe that requires more than one key to open. Instead of a single person having the authority to authorize a transaction, multisig wallets require multiple approvals (signatures) from different people or devices. This added layer of security makes it significantly harder for hackers to gain access to funds.
How Does Multisig Work?
- Multiple Keys: A multisig wallet is set up with several private keys. For instance, you could have three keys in total.
- Approval Requirement: Out of these three keys, a certain number (say, two) must be used together to approve a transaction. This is often referred to as an M-of-N setup, where M is the number of required keys and N is the total number of keys.
- Increased Security: Because multiple keys are required, a hacker would need to compromise several keys simultaneously to gain access, making it a much more secure system compared to a single-signature wallet.
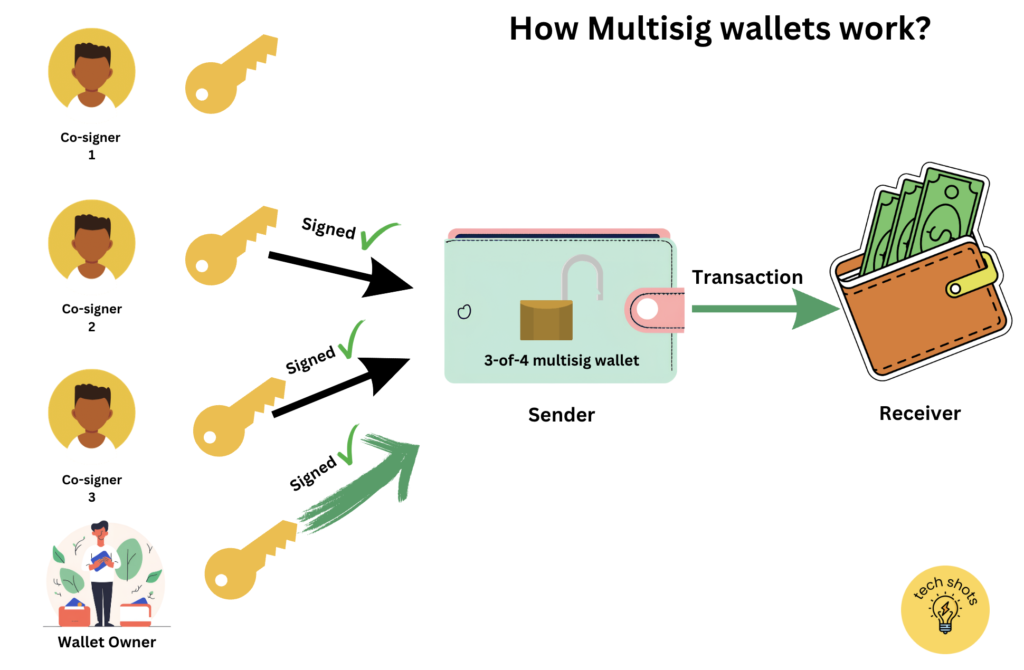
In the above image, a “3-of-4” multisig wallet setup is illustrated, which enhances security by requiring three out of four possible signers to authorize a transaction. In this specific setup, the wallet owner is counted as one of the signers, along with three co-signers. The process works as follows:
- There are four total signers – the wallet owner and three co-signers.
- For a transaction to be approved and executed, three of these four signers must provide their signatures.
- In the depicted scenario, the wallet owner, along with co-signer 2 and co-signer 3, have signed off on the transaction.
- This collective approval (three signatures) meets the required threshold, thus authorizing the transaction to proceed from the sender to the receiver.
Why Use Multisig?
Enhanced Security: The primary benefit of multisig wallets is the increased security they provide. By requiring multiple approvals, the risk of theft is greatly reduced. If one key is compromised, the funds are still safe because the hacker would need access to additional keys to complete a transaction.
Accountability and Control: Multisig wallets are particularly useful for organizations and groups. They ensure that transactions are authorized by multiple parties, promoting accountability and preventing any single individual from having unilateral control over the funds.
Individual Use: For personal investments, multisig wallets add an extra layer of security, protecting assets by requiring multiple verifications before any transaction is approved.
Organizational Use: In organizations, multisig wallets safeguard company funds and ensure that transactions are only executed with the consensus of multiple authorized members, enhancing both security and accountability
Example – How Multisig Works on the WazirX Platform?
WazirX – India’s largest cryptocurrency exchange, provides a platform for users to buy, sell, and trade various digital assets. Known for its user-friendly interface and robust security features, it aims to make cryptocurrency accessible to the Indian market while ensuring the safety of user funds. The platform employs a multisig setup to enhance the security of its users’ assets. Here’s a brief summary of how multisig works on their platform:
- Architecture: WazirX uses a multisig wallet system where control is distributed among several key holders. Typically, this involves five signatories: four from the WazirX team and one from their digital asset custody partner, Liminal.
- Transaction Approval: For any transaction to be approved, a majority (e.g., three out of five) of the signatories must authorize it. This means that even if one key is compromised, the hacker cannot access the funds without the additional approvals.
- Security Measures: WazirX integrates robust security features such as Gnosis Safe for the multisig smart contract platform and a whitelisting policy managed by Liminal. This policy ensures that transactions can only be sent to pre-approved addresses, adding another layer of protection.
In the recent breach (refer news here), hackers exploited a discrepancy between the information displayed on Liminal’s interface and the actual transaction details, managing to manipulate the wallet control which resulted in whopping theft of $230 Million! Despite these measures, this incident underscores the need for continuous improvement and vigilance in security practices.
Conclusion
Multisig wallets represent a powerful tool in enhancing the security of cryptocurrency transactions. By requiring multiple signatures, they add a crucial layer of protection against unauthorized access and theft. Whether you’re an individual looking to secure your digital assets or a company managing a large fund, multisig can provide the peace of mind that your assets are well-protected.
In a world where digital security is increasingly important, understanding and utilizing multisig can make a significant difference. By implementing this technology, you can ensure that your cryptocurrency investments remain safe and secure.
Stay tuned to our blog for more such latest updates and insights.